
The Mechanics of API Vulnerability Chaining
APIs are the backbone of modern web services, they connect databases to front-end interfaces, integrate third-party platforms, and handle massive amounts of sensitive data. Modern applications are ...

APIs are the backbone of modern web services, they connect databases to front-end interfaces, integrate third-party platforms, and handle massive amounts of sensitive data. Modern applications are ...

Payment Card Industry Data Security Standard (PCI DSS) compliance is not optional for organisations that handle credit card information. The latest version, PCI DSS 4.0.1, brings APIs into focus wi...

In modern software architecture, APIs serve as the connective tissue between different systems, enabling applications to communicate and share data. However, as APIs become more prevalent, they als...
Application Programming Interfaces (APIs) have become the backbone of modern web applications, handling everything from user authentication to sensitive data transfers. However, poorly secured APIs...
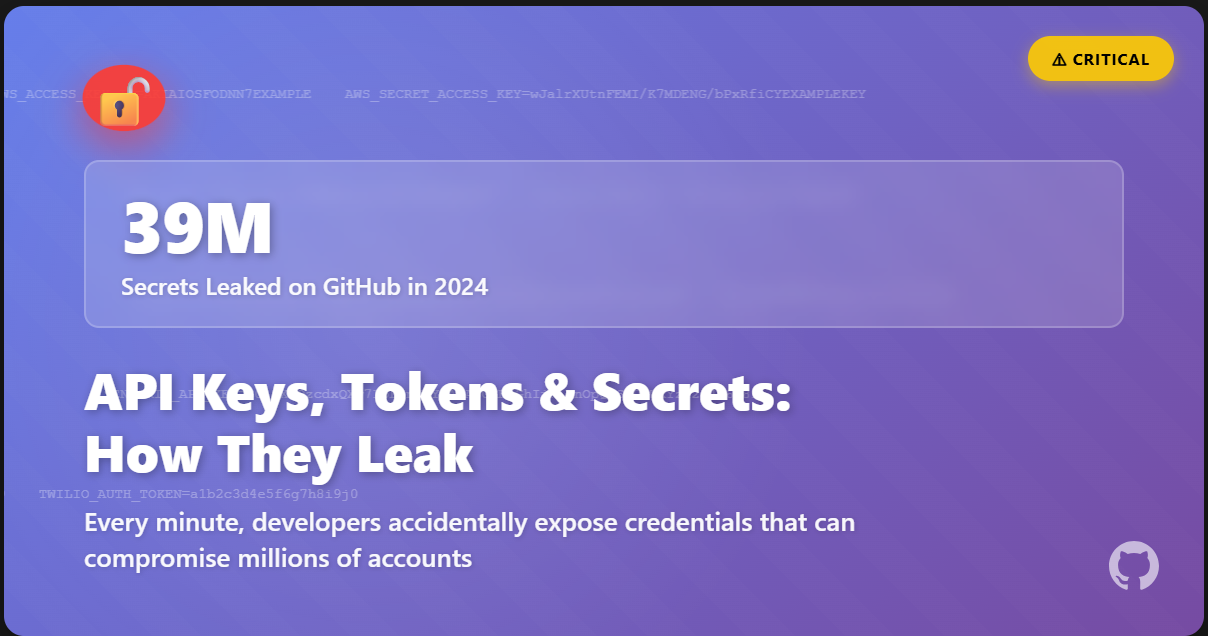
The Scale of the Problem In 2024, GitHub detected over 39 million leaked secrets across its platform [1]. Thirty-nine million API keys, tokens, credentials, and other sensitive authentication data...
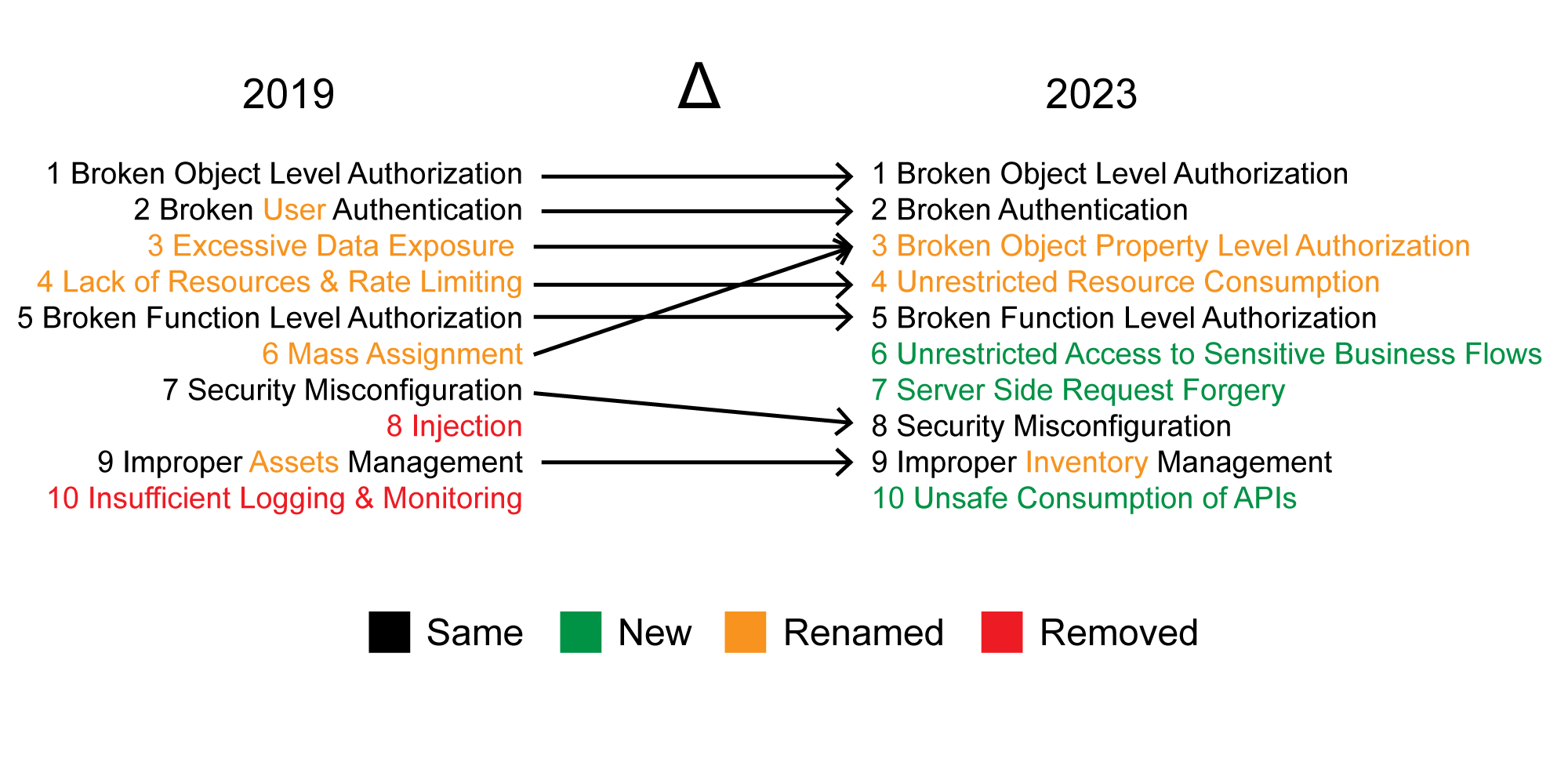
Introduction Broken Object Level Authorization, commonly known as BOLA, sits at the top of the OWASP API Security Top 10 list as API01:2019 and API01:2023. It is the most common vulnerability found...

Earlier this year, researchers discovered a serious vulnerability in the API of the dating app Raw. The flaw allowed anyone to access the personal data (names, dates of birth, preferences) and even...
Recently, I completed the API Security Fundamentals course on APISec University and the experience has been eye-opening. The course covered everything from basic concepts to attack vectors, and I w...
In Part 1 of this series, we deployed the VULN-BANK application to Kubernetes and enforced Pod Security Standards using Kyverno ensuring that all containers ran as non-root users and that default C...

This project involves using a deliberately vulnerable bank application, VULN-BANK by Commando-X (GitHub) and securing its Kubernetes deployment using Kyverno and Open Policy Agent (OPA) Gatekeeper ...